Echo Secure AI Portal
Pioneering the Next Generation of Simulation Platforms

Key Features
Campaign Management
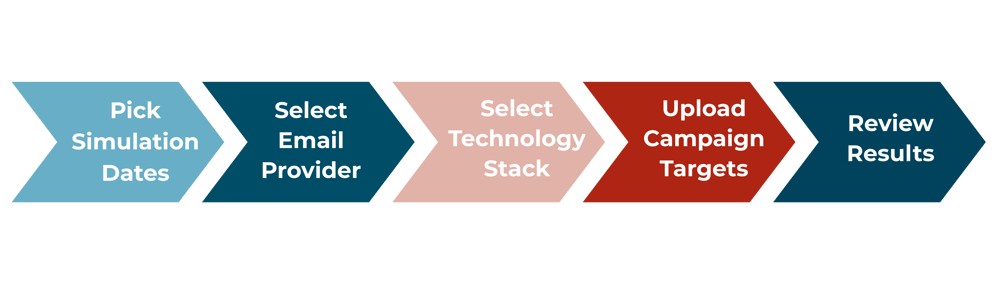
Efficiently plan and organise your phishing simulation campaigns by using our easy 5-step process. This streamlined workflow ensures effective simulation deployment
Real-Time Reporting
Employees interaction is meticulously tracked with each simulation, recording who clicked links, submitted data, opened attachments, and the specific actions taken
Vulnerability Scoring
A holistic scoring metric for each simulation, determined by the aggregate susceptibility of your organisation to the specific phishing tactics employed in the campaign
Trend Analysis
Monitors employee responses over time during regular simulations, informing your broader cybersecurity strategy and measuring improvements for continuous refinement of security policies and processes
Identifying Susceptible Groups and Individuals
Granular analysis of which departments, teams, or even individuals show a higher propensity to interact with phishing attempts and may require focused training
Highlighting Common Failure Points
Detailed insights into which specific types of lures, key behavioural triggers, and attack vectors prove most effective in engaging your employees
Customer Support
Web-based support to assist you with navigating the portal workflow, troubleshooting any technical issues, and addressing any queries you may have
Five-Step Process
Effortlessly schedule and manage phishing simulations in five easy steps through our portal: