Adversarial Phishing Simulations
A New Era of Phishing Simulation

APS applies offensive security principles to think and act like a malicious actor. This is more than just routine compliance simulations. We simulate real threats.
No recycled templates here. APS go beyond sending out generic fake emails and replicates the sophisticated, often targeted attacks that break through traditional defence mechanisms and actually deceive individuals. This is outlined in our APS Kill-Chain.
We believe this proactive approach is crucial for strengthening security posture, better identifying the vulnerabilities in your defences and workforce before the actual attackers do.
Breaking the Cycle for Real-World Impact
Echo Secure addresses a critical issue facing the industry: how to effectively combine platform-based phishing simulation campaigns with intelligent red-teaming tactics. The market today is stagnating; overrun with box-ticking and lacklustre outputs that fail to represent true attacker behaviour. Echo Secure breaks this cycle by using our deep expertise in offensive security to deliver a simulated attack platform unlike anything seen before.
While others concentrate on eliminating 80% of mass phishing attacks, we focus on the 20% - the attacks most likely to actually cause significant financial and reputational damage, as well as serious disruption to operations. The vast majority of successful cyber attacks still begin with phishing. Our simulations treat your employees as a vital line of defence, not just a tick-box.
Relying on traditional security measures is no longer sufficient, Echo Secure is leading the transformation of phishing simulations into a credible, threat-driven discipline, empowering organisations' to truly enhance their security posture.
Offensive Security Principles
Phishing isn’t just a security issue — it’s an operational one. And your defences need to reflect how your organisation actually works, not how a templated platform assumes it does.
This is why we apply Offensive Security Principles to our APS campaigns:
Thinking Like an Attacker
Proactively Identifying Vulnerabilities
Simulating Real-World Attacks
Providing Actionable Recommendations
By combining proactive educational webinars with detailed, data-driven post-simulation analysis and targeted training recommendations, we empower our customers to not only understand their vulnerabilities but also to take concrete steps towards building a more resilient and security-aware workforce. Our goal is to provide the knowledge and tools necessary for continuous improvement in the fight against phishing attacks.
.
Continuous Learning and Adaptation
Just as attackers constantly evolve their tactics, APS operate on a continuous improvement cycle. We regularly conduct simulations to track progress and uncover emerging vulnerabilities.
Crucially, each subsequent APS adapts its content, complexity, and focus based on insights from previous campaigns and the latest threat intelligence. This ensures your defences and workforce are perpetually learning and prepared for the ever-changing threat landscape – a fundamental tenet of effective offensive security.
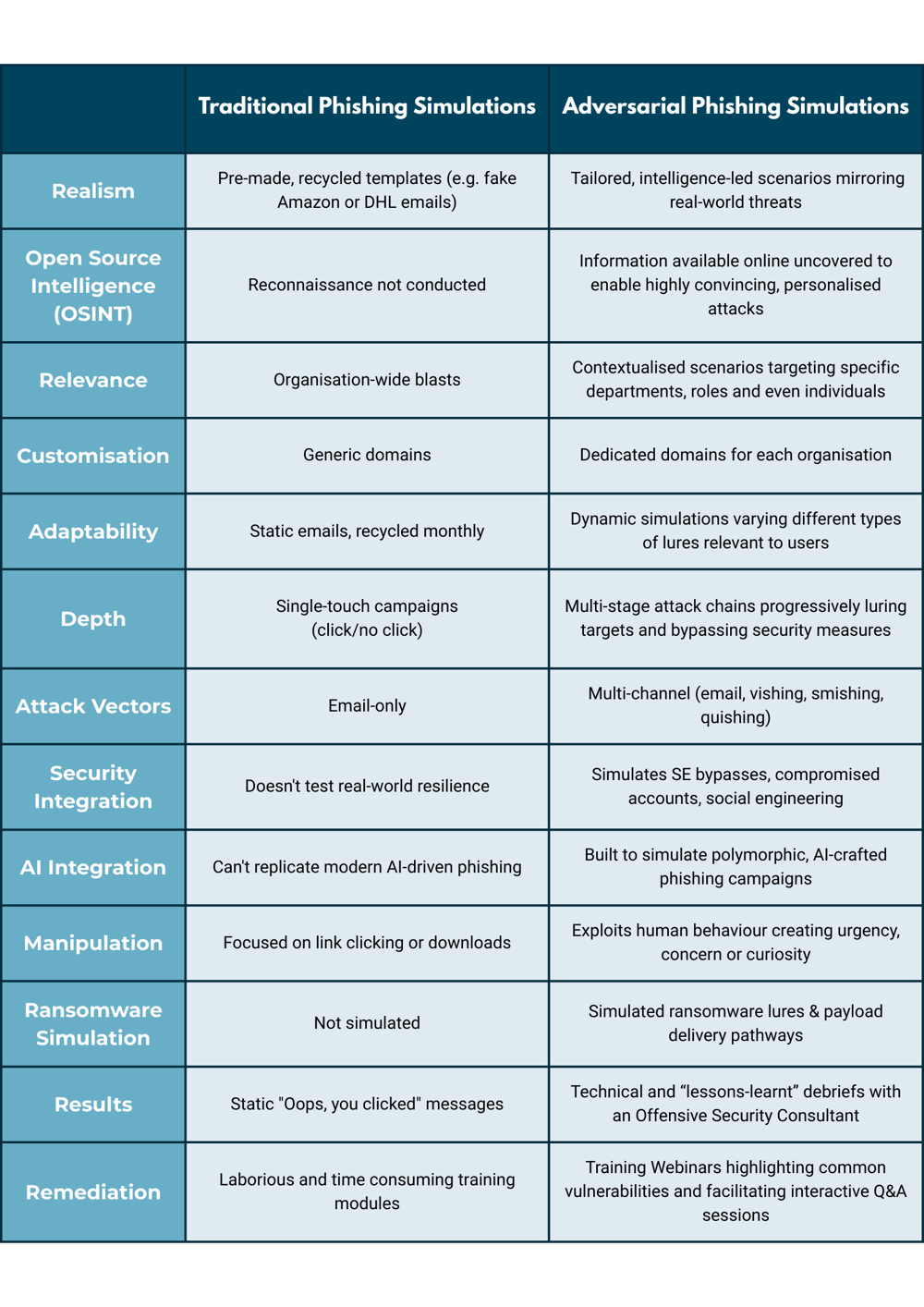
The Advantages of APS Over Traditional Methods
-2.png?width=1000&height=1000&name=Echo%20Secure%20Logo%20(1)-2.png)
-1.png?width=500&height=500&name=Echo%20Secure%20Logo%20(1)-1.png)
